The news that Lenovo pre-installed adware on all consumer laptops sold in the US for the last three months of 2014 (yup, that would be the Thanksgiving through Christmas prime shopping season of the year) is being sadly under-reported by the mainstream press, although the tech press has a better idea of just how much mischief Lenovo did.
The really outrageous point here isn’t that adware came along with the other bloatware that all Windows users suffer from: it’s the fact that this adware was deliberately designed to undermine SSL, which underpins all security on the Internet.
Here’s how SSL is supposed to work: if you connect to Kerika, you are using a secure, encrypted connection to somebody that you genuinely believe is Kerika, Inc. of Issaquah, Washington, United States.
But how do you really know that it’s Kerika on the other end, and not someone pretending to be Kerika?
The only reliable way is to click on the lock icon shown in your browser (whenever you are on a secure SSL connection to any website), and your browser will then tell you who you are connected to, and more importantly, why the browser believes you are actually connected to Kerika and not somebody pretending to be Kerika.
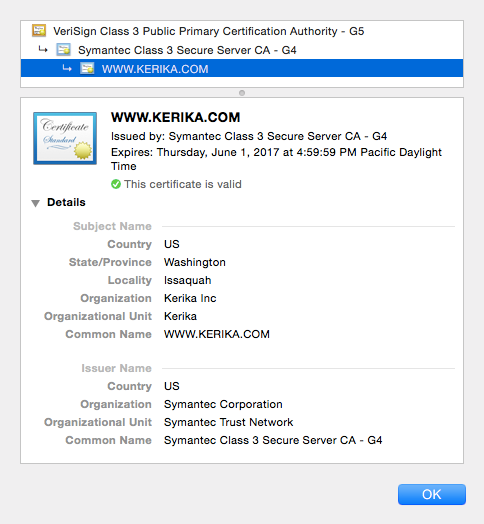
The image above is the actual SSL certificate shown when you connect to Kerika, and then click on the lock icon in your browser.
It says, in effect, that a company called Symantec Corporation is the one that vouches for Kerika’s identity: in other words, it is Symantec Corp. that is assuring you that it really is Kerika that you are connected to, and not somebody pretending to be Kerika.
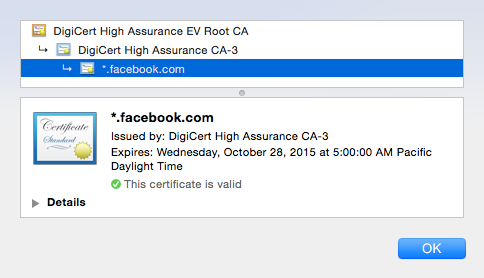
These SSL certificates could be issued by anyone, for example Facebook relies upon a company called DigiCert:
And Bank of America relies upon a company called Verisign:
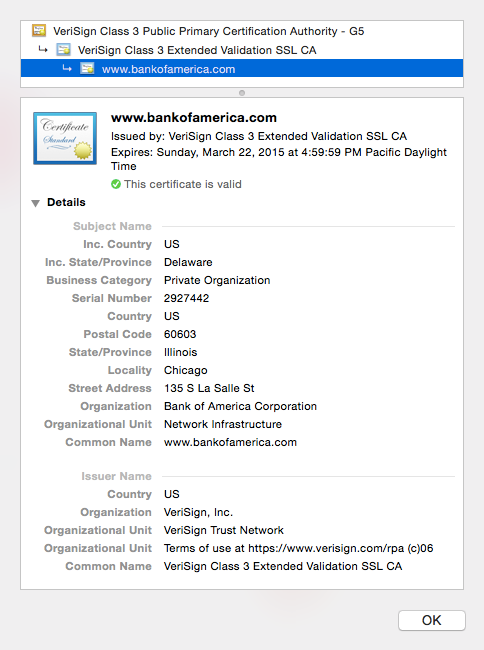
Unless you happen to be using a Lenovo computer that you bought last Christmas, in which case there is a “man-in-the-middle” that you weren’t aware of:
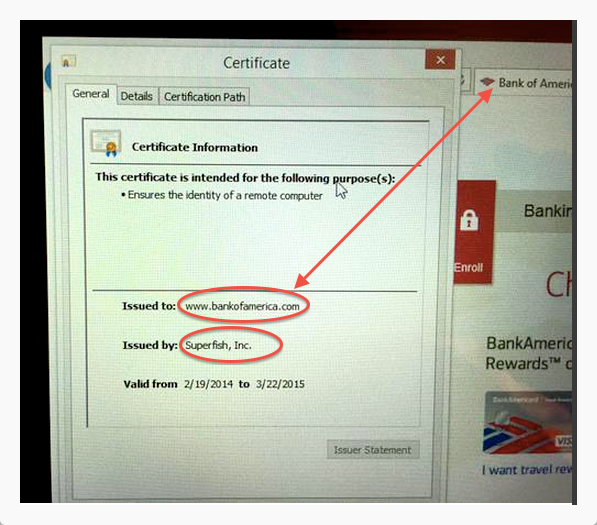
(Above image captured by security researcher Kenn White, @kennwhite)
On this Lenovo computer, an adware company called “Superfish” is the one that’s vouching for Bank of America, which isn’t right at all!
This is a classic “man-in-the-middle” attack scenario: most people would see the lock appear on the browser when connecting to a secure website, like Bank of America’s, and assume that they are safe. Instead, their communications is actually being intercepted by Superfish before it gets to Bank of America.
This is inexcusable, even for the “very minor compensation” that Lenovo got from Superfish.
(And, by the way, this is pretty much how most Windows PC manufacturers make money: there is so much price competition in the Windows market that they all resort to bloatware and adware to juice up their profit margins…)
And because the same piece of adware was distributed on literally thousands of machines, the same private encryption key is being used on all of these machines, which makes it easy for people to use these bogus SSL certificates to create man-in-the-middle attacks on any number of banks and other secure websites.
(And, of course, the private encryption key has already been decrypted, just hours after the news about Lenovo broke this morning.)
All this makes for appalling news for anyone who bought a Lenovo PC towards the end of last year. Merry Christmas.