Thanks to support from Google’s engineers, the problems we had been facing with Kerika’s listing on the G Suite Marketplace has been fixed!
Here we are, in all our glory:
Thanks to support from Google’s engineers, the problems we had been facing with Kerika’s listing on the G Suite Marketplace has been fixed!
Here we are, in all our glory:

We used to have separate button, and associated menus, for actions related to cards and for actions related to columns:
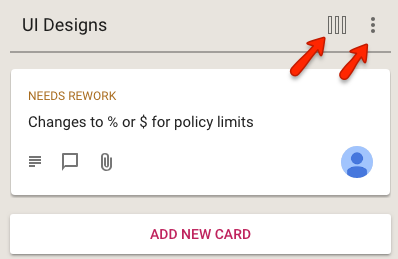
This reflected the history of the Kerika product: we first designed and built the card actions, and much later added the column actions.
In retrospect, however, we concluded that separating these into two separate menus was not a good idea: it was confusing for our users to remember which menu supported which action. (Even the Kerika team, which uses Kerika for everything that the company does, was having trouble remembering the differences between the two buttons and menus.)
We have fixed that usability problem with our latest release: a single button is shown, and the popup menu that appears includes both card actions and column actions:
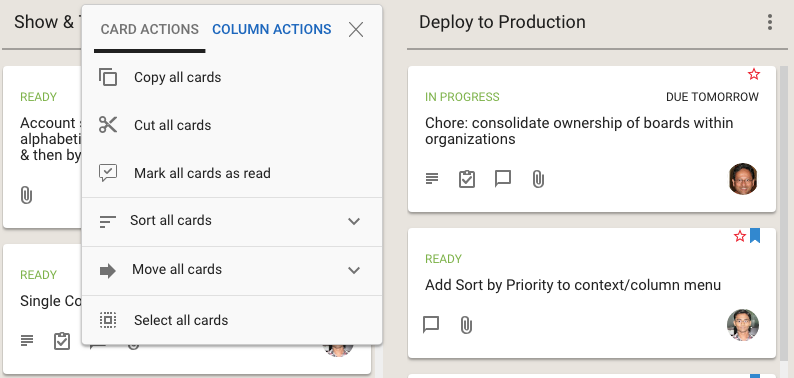
Clicking on the Sort and Move actions brings up all the sorting and moving options you have; the Sort menu now has a much richer set of actions:
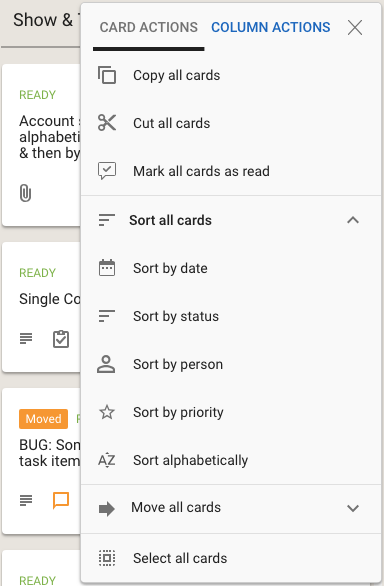
We have also done some small tweaks to the sorting action: Sort by Status now puts the On Hold cards at the bottom of the column, below all the ones flagged as Normal.
About a week ago, the Kerika listing on the G Suite Marketplace disappeared for reasons we still don’t understand. We have been working actively with Google’s engineers to fix this, and are confident they will soon deliver a solution — the problem is on their end, not ours — and in the meantime we would like to apologize to anyone who is affected by this.
The underlying problem is that G Suite Marketplace is transitioning, and right now there are some overlapping systems in place that are creating problems for Kerika (and possibly other third-party apps).
Historically, if you wanted to publish your app on the G Suite Marketplace, you did so using the Chrome Web Store — which is where you also published your app for the Chrome Web Store, obviously.
This always led to to some confusion from our perspective: we had to maintain two identical product listings using the same Chrome Web Store Developer Dashboard. And since this process has been in place, for the past several years, Google itself has been deprecating the use of the Chrome Web Store to distribute browser-based apps through this store.
Meanwhile, the Chrome Web Store Dashboard itself is getting a much-overdue UI makeover, and while this is underway the dashboard doesn’t have all the functionality that the old dashboard does, and there, of course, some bugs remaining in the new dashboard that Google needs to iron out.
(While the old Chrome Web Store Dashboard was ugly as sin, it was old and stable. The new Dashboard is much nicer, but not quite, quite ready yet.)
And there’s also the Google Cloud Platform API Dashboard: newer than the Chrome Web Store Dashboard, and with a completely different user interface and functions, since it manages an app developer’s use of many different cloud services from Google.
This has become another place to maintain your app’s product listing, and this seems to be where our problems originated: the G Suite Marketplace currently takes some information from the Cloud Platform Dashboard, and some information from the Chrome Web Store, to define your product listing.
We have been actively working with Google’s engineers, support and product management to try to resolve this problem — and we are grateful for the attention they have been giving us — and we hope to be out of the woods soon. One unexpected benefit of these problems has been the opportunity to talk to Google about our experience as third-party app developers: hopefully our feedback can help them make the G Suite Marketplace more useful to both Google’s customers and ours :-)
For some segments of our users, e.g. college students using Kerika for their course projects, it makes sense to treat each user as an independent entity, since the relationships between these students will vary from class to class, from semester to semester.
These collaboration networks are very dynamic, and it’s impossible to predict whether a team that got together to work on a three-month class project will stick together after that project is over, or work as the same group of people on the next class project.
In business environments (companies, nonprofits and government agencies), however, the teams are more stable: people don’t change jobs every few months. But, turnover can still be a problem: if Joe leaves your company, how can you be sure that all the boards and documents that Joe had created are not lost along when Joe is gone?
The simple solution to this is to use service accounts to own all the boards that are being used by a community of users, like a department or even the entire company (if the company is small enough).
A service account looks like any other Kerika account — it is associated with it’s own email, e.g. kerika@example.com — but it isn’t actually a real person: the email will have been set up by the organization’s IT staff or management, and the password is typically shared between a small handful of supervisory people.
Unlike real people, service accounts will always stick around: they won’t retire, resign, or get run over by a bus…
This means the organization has continuity and security with respect to it’s Kerika boards and documents: because the project assets are owned by kerika@example.com, rather than joe@example.com, it doesn’t matter whether Joe is still working at the company or not.
We encourage all our professional users — people working in companies, nonprofits and governments — to set up service accounts as a best practice, and we can help you: just email us at support@kerika.com and we will do all the account consolidation for you:
When users have been consolidated within a service account, any new boards that they create will automatically be owned by that service account, rather than by the individual users. This ensures that all current and all future project assets are owned by the service account, i.e. by the company, rather than by individual users.
It’s still possible for individual users to have privacy within the service account: for sensitive work (e.g. personnel matters) they can adjust the privacy of individual boards to be “share with board team only”. When the privacy is set to board team only, the board will be visible only to the people who are specifically added by the Board Admins to the board’s team.
The Account Owner, i.e. the service account, will always have access to every board within that account, regardless of the board’s privacy settings. This is consistent with how other organizational assets are currently managed: if you have a work email, for example, you expect to have privacy from your coworkers, but you know that the company’s IT department will always have access to your email if they need it — and your email doesn’t really belong to you, but to your employer.
If you hide a column from your view of a Task Board or Scrum Board, Kerika now makes it clear whether this column has any cards or not:
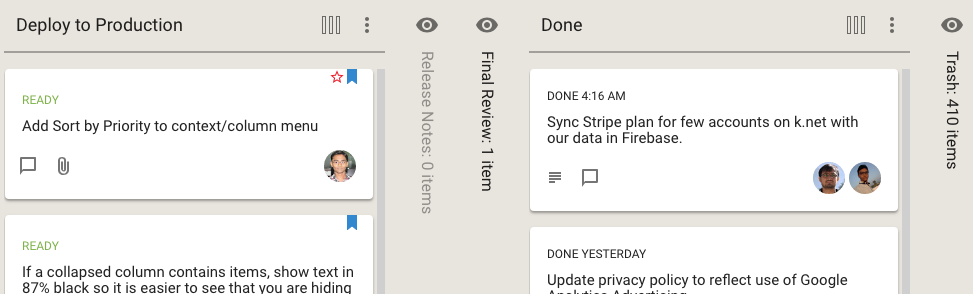
In the example shown above, the Release Notes column is empty, so it is shown in a light shade of grey, while the Final Review column has at least one card, and it is shown in black.
Kerika also helps you see, at a glance, whether the columns you are hiding have any updates you haven’t caught up on, or cards that are overdue:
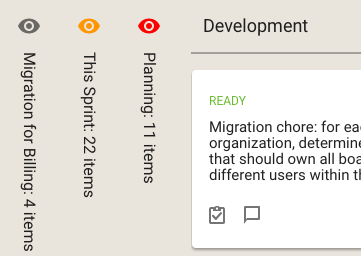
The orange icon in the example above shows that the This Sprint column contains cards with updates on them that you haven’t caught up on yet, and the red icon shows that the Planning column contains overdue cards.
We recently rewrote our Privacy Policy to be more conformant with GDPR, the European regulation on privacy protections for their citizens.
There are no substantive changes: our old Privacy Policy was already very pro-privacy and pro-user, but the language and format has been changed to follow what appears to be the common standard for GDPR-compliant policies.
We have mentioned below the problems we had with GoDaddy’s SSL certificates; we have fixed this by switching to the open-source certificate authority called Let’s Encrypt.
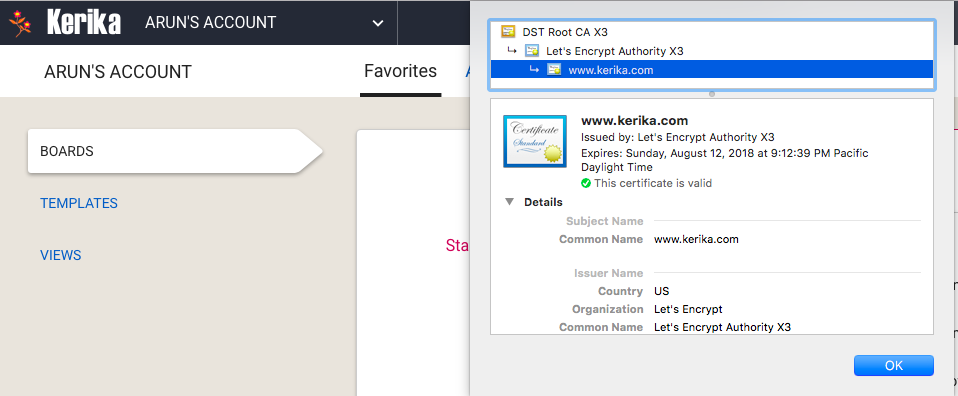
Let’s Encrypt is a free, automated, and open certificate authority brought to you by the non-profit Internet Security Research Group (ISRG). It lets us host our own certificates, so we don’t have to rely upon third parties and can have better control over the quality of our service.
With our latest update, launched over the weekend, we have made some significant changes to how users access multiple Kerika accounts.
The motivation for all this is simple: our old billing mechanism was manual and error-prone. It was difficult to track which accounts had paid for subscriptions and to ensure that subscriptions were renewed in a timely manner.
So we are moving to an completely automated system that will allow our customers to manage their subscriptions more easily, make online or offline purchases, and manage their account teams.
We are about halfway there: we have done the changes to the account management piece, and have some more work before the billing system is ready.
One consequence of this is the way you view your Home Page has changed: the Home will now always show the boards and templates that related to a single account, rather than across multiple accounts.
(Previously there were three buckets: Favorites, Owned by Me, and Shared With Me.)
Switching between all your open boards, and all your accounts, has been consolidated into a single Account Switcher function that appears on the top-left corner of the Kerika app, where the old Board Switcher used to be:
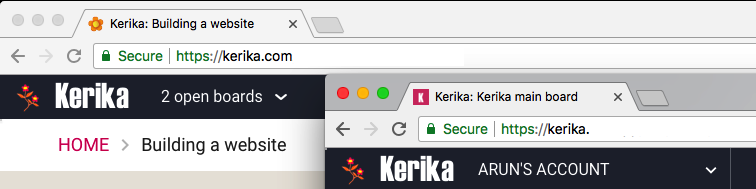
Clicking on the Account Switcher will let you switch between boards, and between accounts:
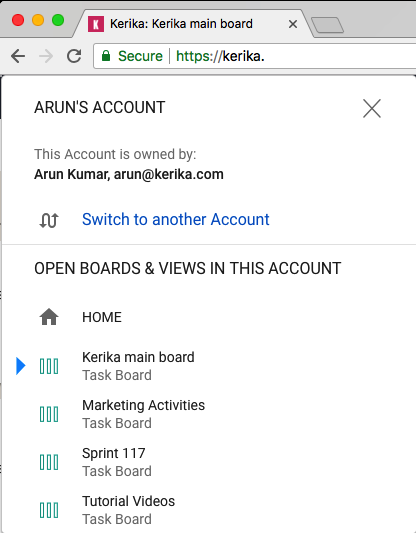
Calendar syncing and Preferences are now applied on an account level, so if you are working in multiple accounts, you can choose to have different preferences for each account.
You can access your Calendar and Preferences settings by clicking on your face on the upper-right corner of the Kerika app:

With this change, it becomes more important for organizations to consolidate ownership of all their boards within a single account. You can do this yourself, by selecting boards from your Home Page and using the Move to Another Account function:
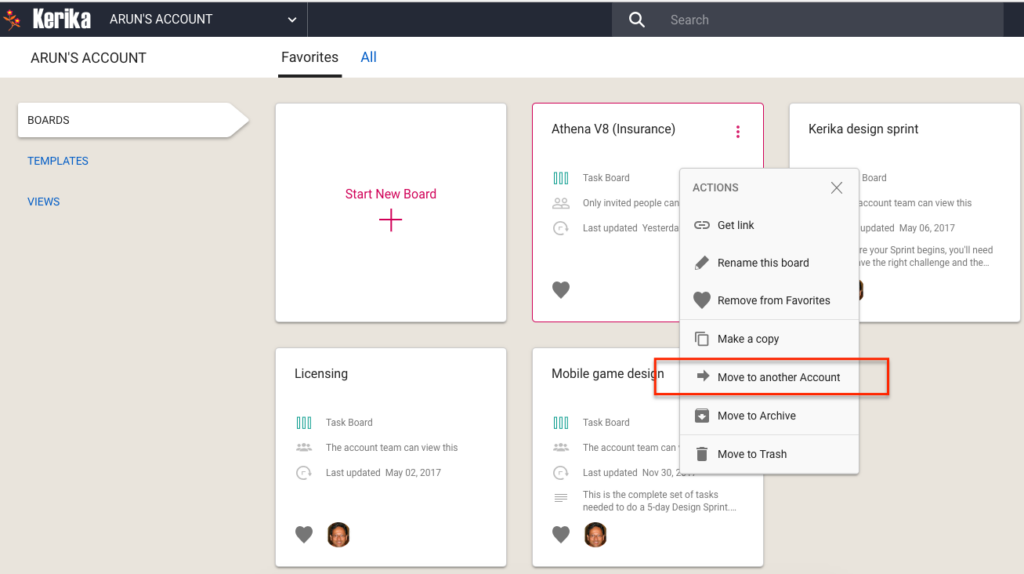
You can also let us do this for you: just contact us at support@kerika.com, and let us know which accounts you would like to consolidate and we can do all the work.