We made it easier to see, at a glance, which boards have unread updates when you are at your Kerika Home page:
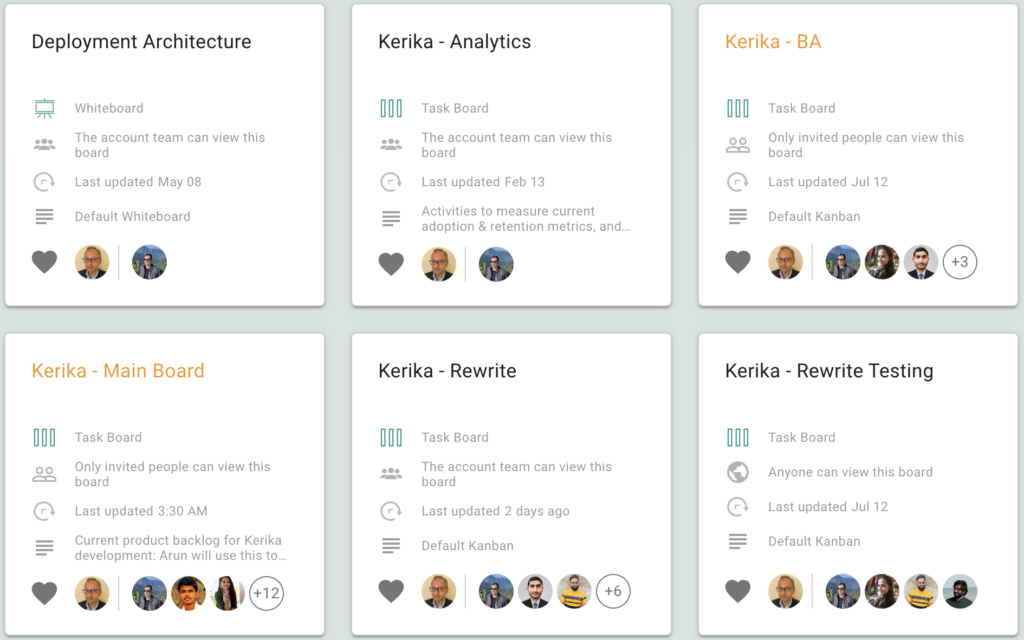
Boards with updates on them that you haven’t caught up on are indicated with orange text for their titles.
We made it easier to see, at a glance, which boards have unread updates when you are at your Kerika Home page:

Boards with updates on them that you haven’t caught up on are indicated with orange text for their titles.
The What Got Done View, that’s accessible from your Dashboard, now has a new feature: it can show you everything that got done by calendar quarter:
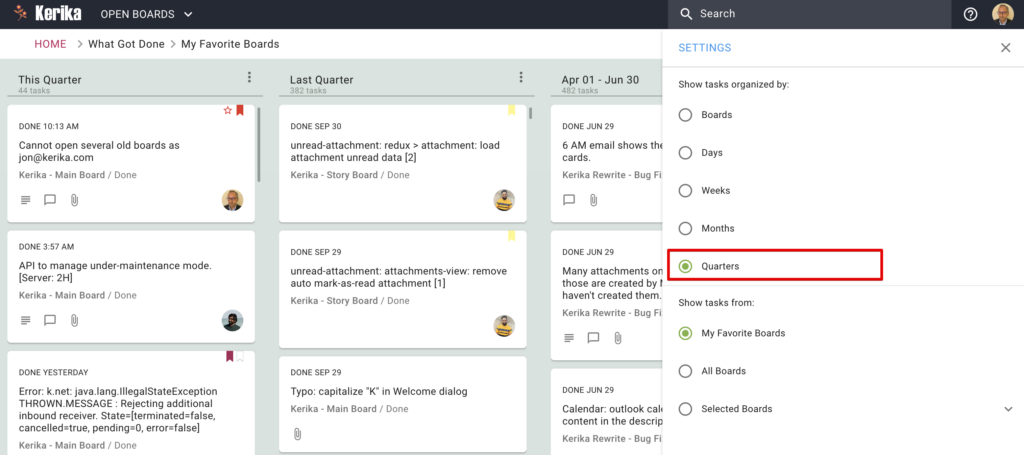
This can be accessed from the Settings dialog from this View: just click on the gear icon at the top right corner of the app.
This feature is also available for the What’s Due View: now you can see how your long-term deliverables stack up over the next four quarters.
This By Quarter View should help folks that need to report to their bosses what the team is getting done, on a quarterly basis.
“Kerika just got better…” is a message you are seeing almost daily, and that’s thanks to the massive 2-year effort that overhauled our old backend and made it much easier to push out changes.
We are now rolling out bug fixes and feature improvements on a daily basis, using our modern architecture. Previously we had to batch these up and do large upgrades; now we can push out the smallest changes, when we feel they are ready to go.
Under the old architecture taking the servers down for maintenance was a painful necessity; now changes can be deployed without any downtime.
All changes still go through extensive internal testing, and new features go through a lot of usability testing in particular, before anything gets pushed out.
When you include a URL in a task’s details tab or chat, Kerika will look up the URL and then display the title of the page. This is really useful because the URL may be very long and generally unintelligible, and people find the name of the site to be more useful.
Here’s an example, where the URL for the New York Times website is included in a chat message: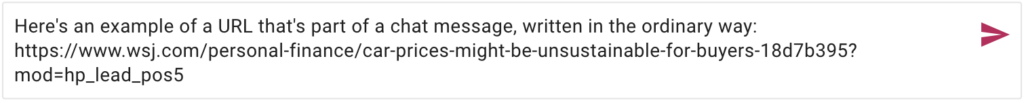
After this chat is sent, Kerika will look up the URL and then use the site’s name when the chat is displayed in Kerika, like this: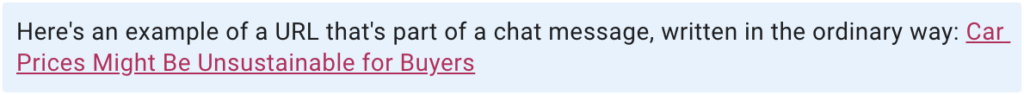
This is useful most of the time. The original URL, from the Wall Street Journal was long and contained many characters as a suffix that most people would not find helpful.
But sometimes you want the URL itself to be clearly visible, and that’s possible in Kerika if you use the special escape character called the tilde “`” which appears on the top-left corner of English keyboards.
Here’s how you would use the tilde to “escape” the URL you are referencing:
And this is how it would look in the chat stream:
Because you used the tilde character to bracket the URL, Kerika doesn’t try to show the name; instead it shows the URL exactly as it is.
Another useful improvement from Kerika :-)
An effort that took 2 years finally completed yesterday when we updated the Kerika app.
This massive project involved rewriting everything on the back-end of Kerika in order to modernize the architecture and set up us for a more rapid development of end-user functionality, as well as making it easier to release new versions in the future using Docker container.
Our old backend was not well designed: everything ran as a single monolithic server. Over the years we moved slowly away from that, by building new features as microservices, and while that helped a little, it wasn’t enough.
We had reached a point where it was taking exponentially more time to build new features, and we were facing operational risk as well because the old backend was poorly understood and document.
A complete rewrite was necessary, and we bit the bullet on that a couple of years ago. There was significant cost and complexity but our great team powered through all the challenges, particularly when it came to transitioning our main database away from MySQL (hosted as RDS, by Amazon) to a NoSQL model using Google’s Firestore service.
Now that we are done we can start delivering more functionality, starting with support for non-English languages.
Stay tuned for our first non-English language, which will be Hindi, to be offered in a couple of weeks.
The transition to remote work has been swift, and digital tools have become the backbone of modern workplaces. However, the landscape of remote work is still fairly new and many teams are still far from their greatest potential. Still, if they polish their processes, remote teams can be as productive as they would on-site, and even more. This article will present digital tools essential to optimize digital workplace workflows and productivity.
Project management tools are the backbone of any team’s workflow. Project management tools centralize your team’s tasks and projects, enabling employees to manage tasks, deadlines, and resources.
Use a project manager to track progress and identify any bottlenecks. Likewise, logging tasks and project information adds a layer of transparency and accountability to project management tools.
In any case, your workflow can only be as good as the project management software you use allows you to. Some of the most popular project management tools available include Asana, Trello, and Basecamp. However, Kerika stands out from the rest by its own merits.
Kerika is a powerful project management tool that helps teams work efficiently and collaboratively. It offers a variety of features to meet the requirements of the most demanding users. Here are some of the features that make Kerika a must-have tool for any digital workplace:
File-sharing software enables employees to store and work with files no matter where they are located and from multiple devices. Such flexibility reduces the time and effort needed to search for documents or to track down the latest version of a file, something methodic and disorganized employees enjoy alike.
File-sharing tools such as Google Drive also enable multiple people to collaborate on the same document simultaneously, opening the possibility of real-time feedback and faster completion of tasks. In like manner, users can easily leave comments and make suggestions.
Administrators can easily control who has access to specific files or folders, ensuring that confidential information is kept secure. Permissions can be set to allow different levels of access to different users, making it easy to share files with only those who need to see them.
Effective communication is key to a successful digital workplace. With communication platforms such as Slack, Microsoft Teams, and Zoom, team members can stay connected and work together seamlessly through video and audio calls, and screen and file sharing.
On the other hand, video conferencing tools with virtual reality (VR) technology are a more cutting-edge option. VRth finds industrial applications in industries such as architecture and engineering by allowing teams to visualize and interact with 3D models Yet, VR can also work as a space for brainstorming, meetings, and events. To know more about VR meeting platforms, check Virbela and NextMeet.
Cybersecurity tools such as firewalls, and intrusion detection systems help businesses to protect their data from cyber threats. On the other hand, these tools also help businesses to comply with data protection regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
Additionally, virtual private networks (VPNs) are essential for any business that values data privacy and security. VPNs create a secure and encrypted connection between a business’s network and the internet, preventing unauthorized access to sensitive information. VPNs are especially important for remote workers who need to access company resources from outside the office. Here is a list of some of the cheapest VPNs.
Business process management software can help businesses streamline their operations by automating repetitive tasks and workflows, including data entry, invoice processing, and customer service.
Besides, artificial intelligence (AI) technology is increasingly being used to improve productivity in the digital workplace, taking care of complex tasks and clearing humans from them. AI-powered productivity tools can help automate tasks, provide personalized insights and recommendations, and analyze data to identify opportunities for improvement. Tools of this kind include beautiful.ai, for coming up with presentations, and Mem made to organize information.
Mind mapping software can help teams visualize and organize complex ideas and concepts through brainstorming, planning, and collaborating. Among popular mind-mapping tools, we find MindMeister, MindManager, and XMind.
On the other hand, digital whiteboards can help teams collaborate and brainstorm more effectively, especially in remote settings: Visualize ideas by drawing or writing them, or share them with others and receive feedback. Popular digital whiteboard tools include Miro, Google Jamboard, and Microsoft Whiteboard.
Guest post from Cybernews.com
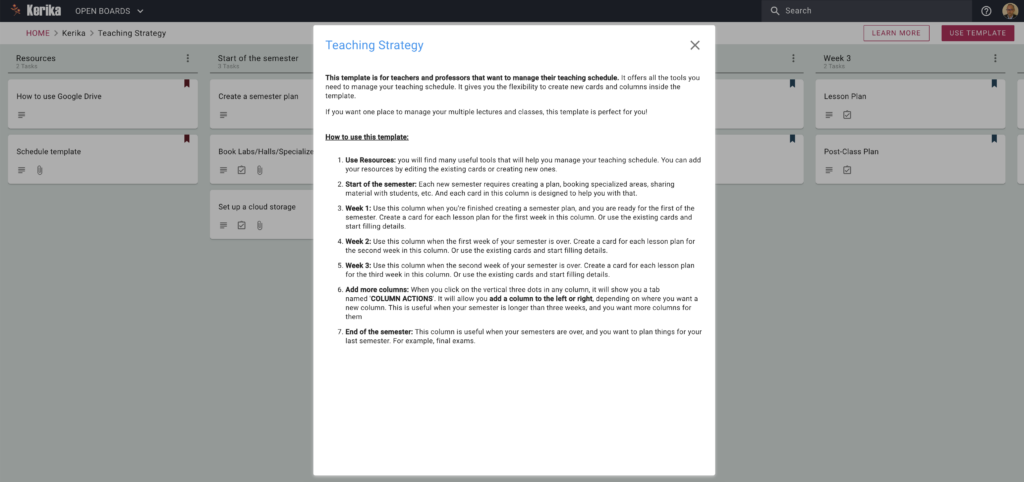
This template is for teachers and professors that want to manage their teaching schedule. It offers all the tools you need to manage your teaching schedule. It gives you the flexibility to create new cards and columns inside the template.
If you want one place to manage your multiple lectures and classes, this template is perfect for you!
How to use this template:
If you’re a business owner or a freelance content writer, it’s important to have a content strategy. Without a solid content strategy, you end up wasting a lot of time managing your content.
By having a solid plan and sticking to it, you won’t have to spend time coming up with new ideas or scrambling to meet deadlines. One of the best ways to build a content strategy is to use a content planner.
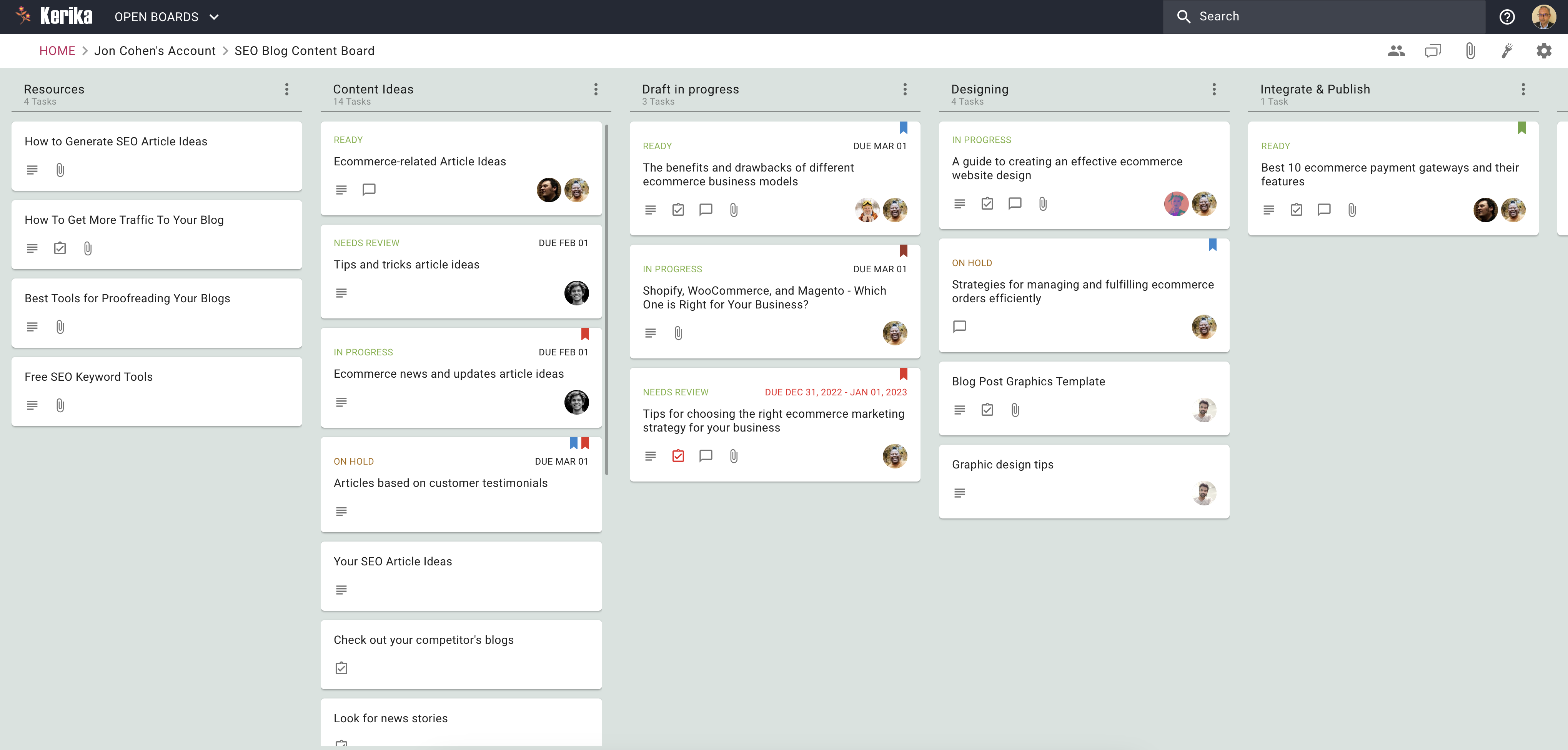
Whether you’re working alone or with a team, a good content planner can really boost your productivity. So, let’s see how this company uses a content planner to plan and publish its SEO content.
If you found this board interesting, here’s a free Template from Kerika that you can use to set up your own board in just seconds:
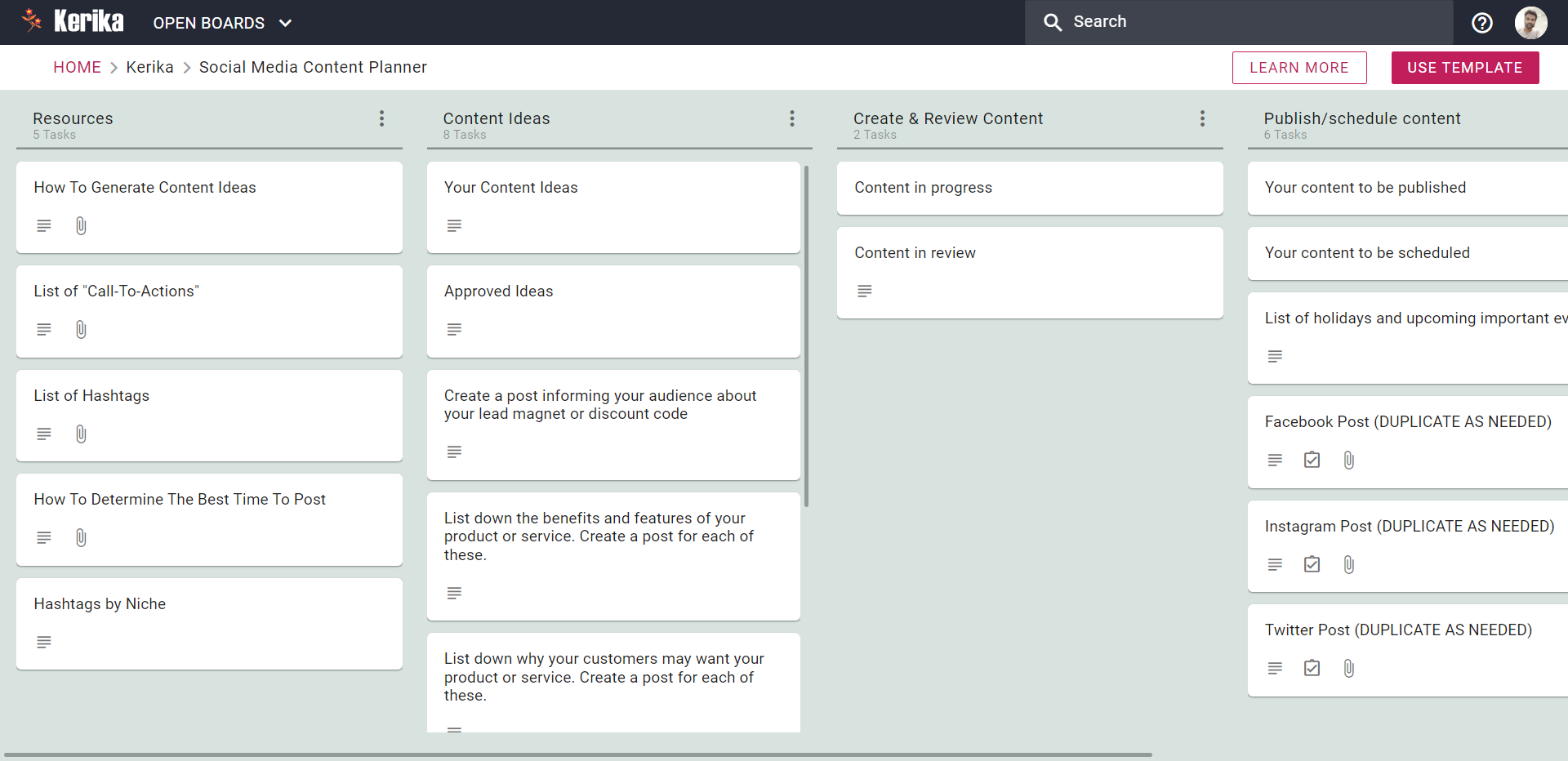
The rest of this article will walk you through the process of using this template:
If you’re a serious content writer, you already know the importance of gathering resources before you start writing. After all, you need to have something to write about!
One of the best ways to manage your gathered resources is to use a Content Planner. A Content Planner can help you organize your thoughts and ideas, and it can also help you find new and relevant information to write about.
Before you start writing, you need to have an idea of what you want to write about. Make a list of content ideas that you think would be popular with your audience.
You can get content ideas by checking out your competitors, looking for news stories, looking for guest post ideas, and brainstorming ideas with your team.
Now it’s time to start writing your content. Keep your keywords in mind as you write and try to include them naturally in your text.
Graphics in blogs capture your reader’s attention, communicate your message more clearly, and overall make your blog more visually appealing.
Once the article is ready, the next step is to add graphics to it. Graphics are important to capture your reader’s attention and make your blog more visually appealing.
Once you’re finished writing, you need to integrate your content into your website. You can do this by adding a blog to your website or by scheduling your content to be published on your website later on.
Finally, you need to promote your content. You can do this by sharing it on social media, writing guest posts on other blogs, or by paying for advertising.
If you’re a business owner or a freelance content writer, it’s important to have a content strategy. Without a solid content strategy, you end up wasting a lot of time managing your content.
By having a solid plan and sticking to it, you won’t have to spend time coming up with new ideas or scrambling to meet deadlines. One of the best ways to build a content strategy is to use a content planner.
Whether you’re working alone or with a team, a good content planner can really boost your productivity. So, let’s see how this company uses a content planner to plan and publish its SEO content.
If you’re a serious content writer, then you already know the importance of gathering resources before you start writing. After all, you need to have something to write about!
One of the best ways to manage your gathered resources is to use a content planner. A content planner can help you organize your thoughts and ideas, and it can also help you find new and relevant information to write about.
Before you start writing, you need to have an idea of what you want to write about. Make a list of content ideas that you think would be popular with your audience.
You can get content ideas by checking out your competitors, looking for news stories, looking for guest post ideas, and brainstorming ideas with your team.
Without SEO-optimized content, your articles and blog posts will never be seen by search engines, and you will never get the traffic you desire. Therefore, you need a solid SEO strategy.
Now it’s time to start writing your content. Keep your keywords in mind as you write and try to include them naturally in your text.
Graphics in blogs capture your reader’s attention, communicate your message more clearly, and overall make your blog more visually appealing.
Once the article is ready, the next step is to add graphics to it. Graphics are important to capture your reader’s attention and make your blog more visually appealing.
Once you’re finished writing, you need to integrate your content into your website. You can do this by adding a blog to your website or by scheduling your content to be published on your website later on.
Finally, you need to promote your content. You can do this by sharing it on social media, writing guest posts on other blogs, or by paying for advertising.
If you want to set up a board like this, we have a free Template ready for you.
From the moment a new hire walks in the door, they start forming opinions about your company culture, their role within the organization, and what it will be like to work for you. That’s why when it comes to hiring new employees, first impressions matter.
When done correctly, on-boarding can help new hires feel welcome, valued, and prepared to do their best work. But when done poorly, there are a lot of things that could go wrong. Here are a few tips to help make your on-boarding process as smooth as possible:
Before you bring a new employee on board, it’s important to run a background check. This will help you verify that the person is who they say they are and that they don’t have any red flags in their past that could negatively impact your business.
A background check can also give you peace of mind that you’re making the best hiring decision possible. To know about a candidate, you need a process that ensures the new employee is the right fit for the job. Check out how this company conducts a background check for its new employees.
When it comes to bringing on new employees, it’s important to do your due diligence and check their business references. This will help you get a better sense of their work ethic and what they’re capable of.
Personal references can give you valuable insights into an applicant’s character, work ethic and overall suitability for the job. They can also alert you to any red flags that might not be apparent from their resume or cover letter.
Asking for personal references is a simple but effective way to screen applicants and make sure you’re making the best possible hiring decision.
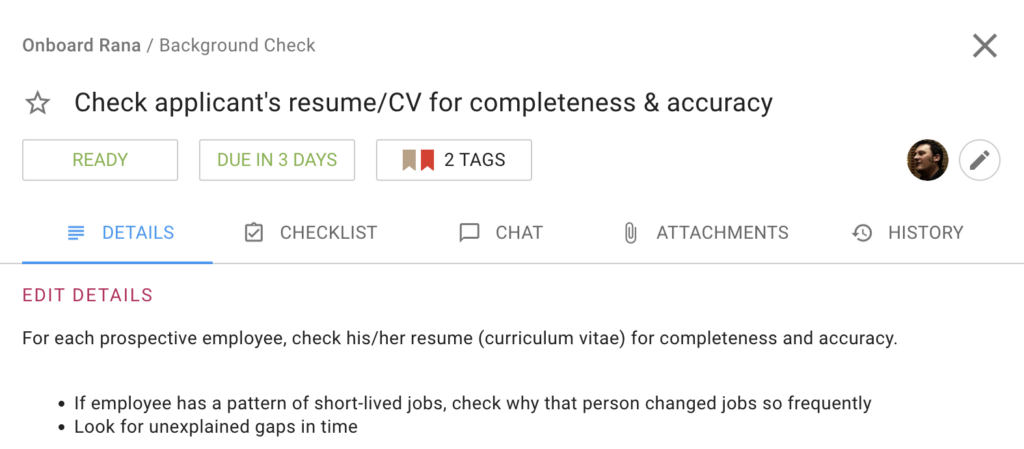
While on-boarding a new employee, it’s important to check their resume or CV for completeness and accuracy. This will help you ensure that there are no discrepancies in their work history.
If you find any inaccuracies, be sure to follow up with the employee to get clarification. It’s also a good idea to run a background check to verify the information on the resume. By taking these precautions, you can help ensure a successful on-boarding process for your new employee.
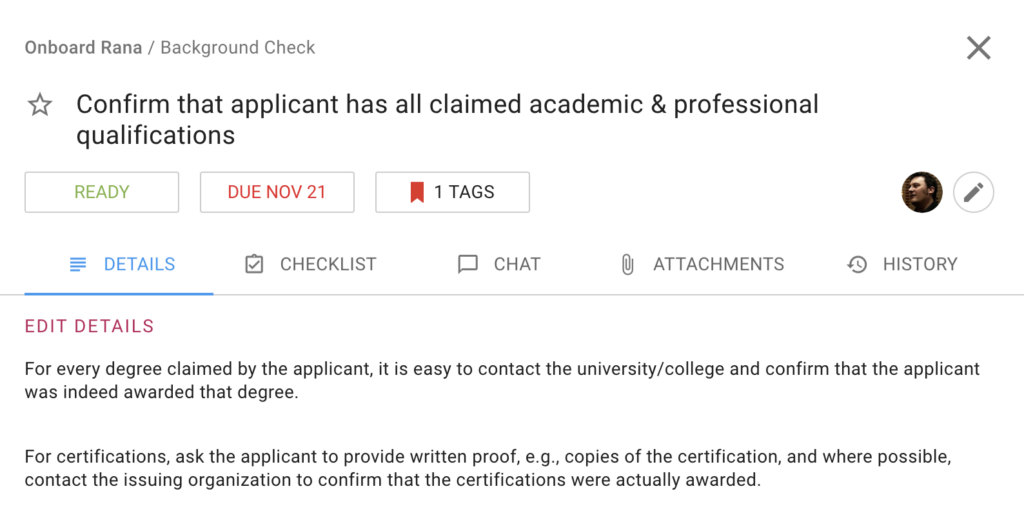
It’s always a good idea to confirm that an applicant has all of the claimed academic and professional qualifications before onboarding a new employee. This can help ensure that the individual is qualified for the role and can help avoid any potential issues down the road.
There are a few ways to go about doing this, such as contacting references or requesting transcripts. Take the time to do your due diligence and it will pay off in the long run.
Credit checks are an important part of the onboarding process for new employees. They help employers to verify an applicant’s identity and to ensure that the person is who they say they are. Credit checks also help to determine an applicant’s financial stability and to assess their risk of defaulting on their financial obligations.
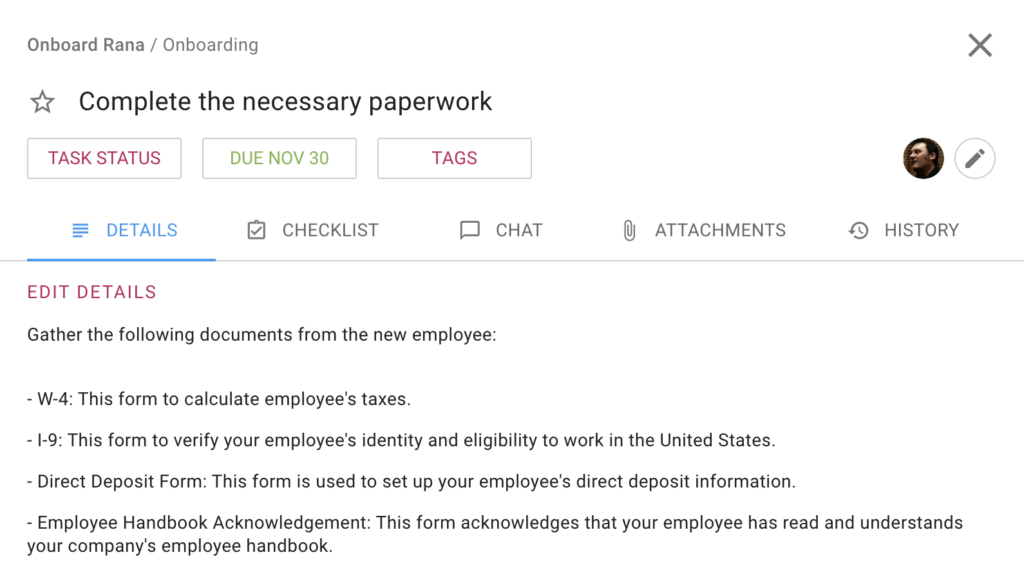
Make sure you have all the necessary paperwork in order before the new employee starts. Here is a good example of how a US-based company collects all the necessary paperwork upfront from a new employee. The paperwork includes the W-4 form to calculate taxes, the I-9: form to verify the employee’s identity and eligibility to work in the US, the direct deposit form, and the employee handbook acknowledgment.
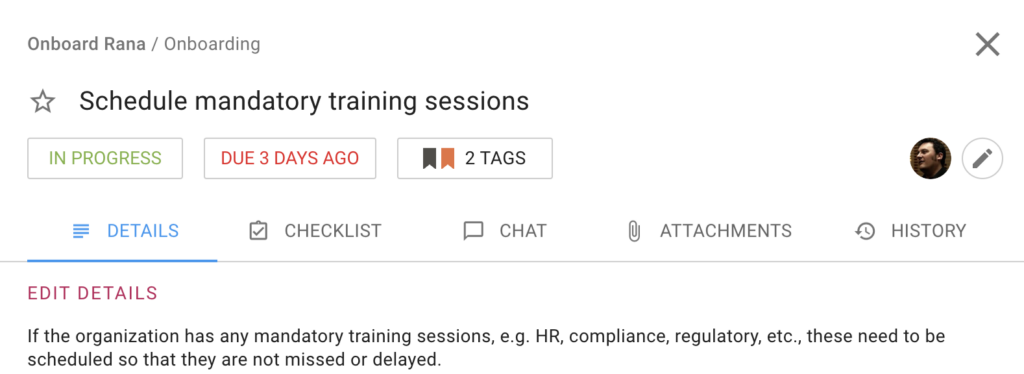
New employees should know what is expected of them in their new role, and the best way to do this is to set up an Orientation Program and Schedule mandatory training sessions.
The Orientation Program is a great opportunity for employees to learn more about their role, and ask questions and get to know their colleagues.
For the Orientation Program to go smoothly, choose a date and time that work for both you and the employee. You’ll want to make sure the program is informative and engaging. If your new employee feels welcomed and comfortable, they’ll be more likely to hit the ground running and be productive from day one.
Training sessions for compliance and regulation are important for several reasons. First, they ensure that new employees understand the company’s policies and procedures from the day one.
Second, they help to ensure that employees are up-to-date on any changes in the law that may affect their job.
Finally, training sessions provide an opportunity for employees to ask questions and get clarification on any points that are unclear.
New employees should feel informed about their role, the company, and the team they’ll be working with. In the following example, the HR has organized a team lunch. This is a great to way to introduce a new employee, this gives a employees get to know each other well.
The department is also getting introduced to the new employee, and this is just as important. So a formal announcement about the new employee, helps existing employee know them better.
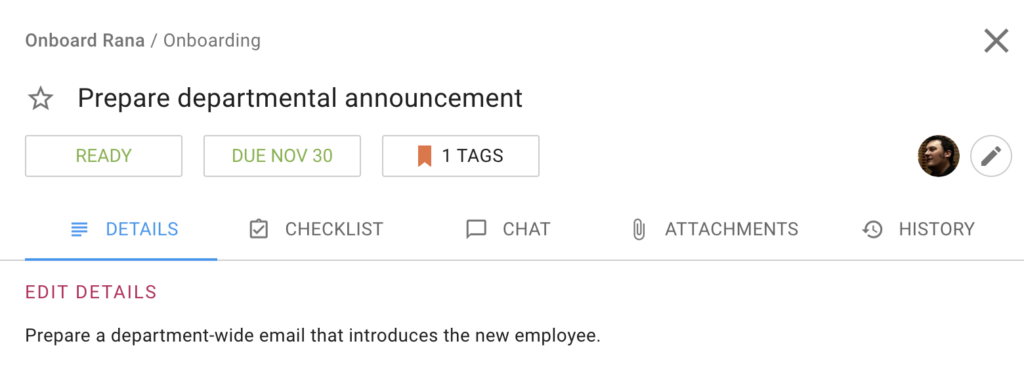
And last, but not least, don’t forget a Team Lunch on Day One!
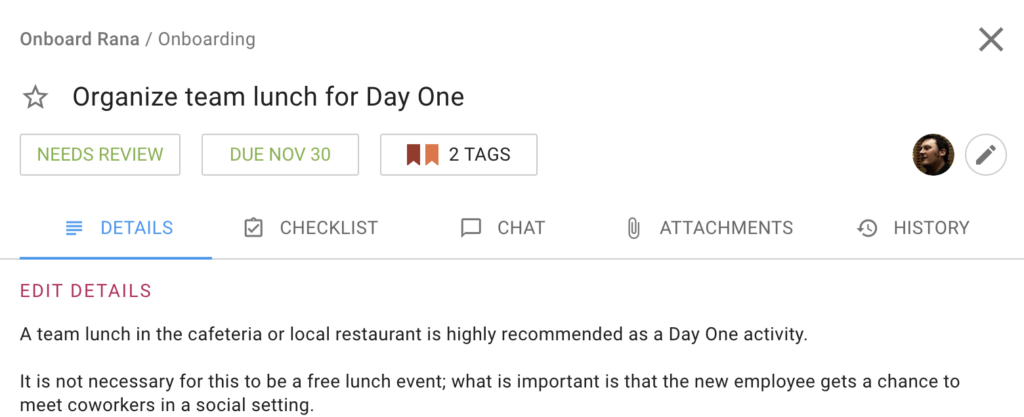
If you want to set up a Task Board for this, we have a free template ready for you.